Swing and a miss
It’s low and away.
The count’s oh and two.
The coldest winter I ever spent
Archive for January 2010
It’s low and away.
The count’s oh and two.
Last night I reported how “it was on fire when I got here“. Well today, I get to report how my neighbor’s apartment caught on fire, nearly burning my building down.
Yipe.
I’ll write more later but the short form is:
I called 911 at 11:23am
The first thing they brought out was a smoldering mattress
nobody hurt
fire limited to 1/4 of one apartment, surprisingly little, maybe 1/4 the stuff in the place is smoke damaged.

Ok, they’re rude. But they’re funny. They are.
I’ve loved this list for years. I remember when Luke Sullivan started quoting them at me with funny faces. I laughed and laughed! Though, truth be told, I was and am jealous that he has such an awesome memory… he could quote most (all?) of this list from memory!
Don’t explain, just tell these to your friends, one at a time with a slow wry grin until they make a disgusted face at you.
My friend Marcus, the founder of the Berkeley Revolution is at this moment in New Zealand with his unicycle basketball team having a blast playing against all the best unicycle basketball teams in the world!
local version:
He is at Unicom, The 15th International Unicycling Convention and Championships held in Wellington New Zealand this year!
I just read news and see that they are doing quite well in the standings. Of course, it’s much more about the journey and having fun, but it feels good to know that Berkeley is representin’!
From their website:
We won our second game 44-2 over NT Cyclones, and we won our 3rd game 32-6 over RSD United, a German team. RSD United gave us a game for a while, we were up just 6-4 at one point–they have some of the world’s fastest unicyclists. But things are going well so far. Tomorrow morning we play probably our toughest prelim, …against a French team (CYCL’HOP), and in the afternoon we will have our first quarterfinal game.
Marcus is 4th from left in the photo
Christmas trees burning on Ocean Beach
 As I stood on one side of the street, a cadre of Christmas tree bearing revellers trotted across the street, passing the ranger’s police car. He came on the PA and meekly said “Put those trees down, we’re going to be arresting people real soon.” The last two words trailed off in that “I wish it were true” tone of voice. He might as well have ended with upspeak. I’m sad that I’m the only person that heard him say it. Corey was in with the cadre and he only heard the first half of the plea, taking the tree I gave him over the hill to the already raging bonfire.
As I stood on one side of the street, a cadre of Christmas tree bearing revellers trotted across the street, passing the ranger’s police car. He came on the PA and meekly said “Put those trees down, we’re going to be arresting people real soon.” The last two words trailed off in that “I wish it were true” tone of voice. He might as well have ended with upspeak. I’m sad that I’m the only person that heard him say it. Corey was in with the cadre and he only heard the first half of the plea, taking the tree I gave him over the hill to the already raging bonfire.
I want to thank Michael Prados for the beer, Jon for the happy wave, Jean and Ben for the conversation, Corey for his blatent disregard for the law, Rick for his balancing tree act and Charlotte for everything.
Q: When you are in your local coffee shop sipping on a latte, surfing the web, what prevents your neighbor three rows over from stealing the internet passwords you type in?
A: Nothing!
If you go to web sites that start out “https://”, (the “s” is the important part), you’re safe. But if you log in to non-secure sites, which happens all the time, your neighbors can “sniff” the network and see exactly what you are doing. To protect yourself, you need to use some kind of security. To get all geeky on you, I’m going to describe using a proxy through SSH tunneling, or possibly described as making a VPN to the cloud.
I took this content from Shanghai Web Hosting. He’s got some good geekery content there. Check it out. I’ve tried it myself and it took just a few minutes to get it going. If you are baffled by this but are worried, and you’re a friend of mine, then call me!
I used my web host provider, Dreamhost as the tunnel server. If you don’t have a web hosting provider (IE a company that hosts a web site like Dreamhost hosts Lee.org for me), then… umm.. that’s another issue.
In brief, here’s what happens when you use this system
————————————————–
As SSH is inherently tunnel-enabled for setting up socks5 proxy servers, you can instantly turn your personal computer into a socks5 proxy server by the help of PuTTY through your web hosting server, breaking through firewalls. The idea is to direct all traffic from your local computer browser through PuTTY SSH session to the web hosting server and back from it.
Here we go:
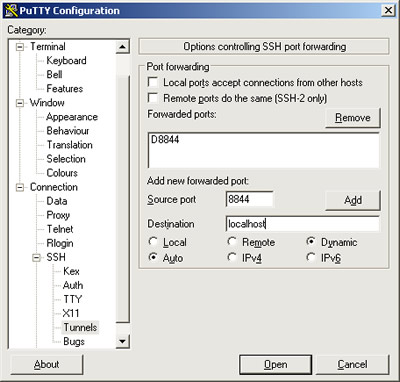
Leave the SSH session open and your personal computer has now become a socks5 proxy server. Open your favorite browser, for example, FF3:
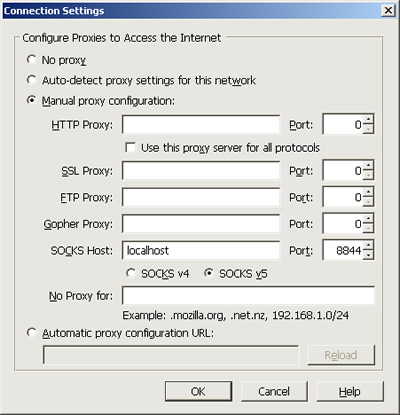
Remember though, that all traffic you use by browsing the web pages and downloading whatever stuff by the local proxy goes through your web hosting server and will be counted on the hosting bills.
Exciting! Now you’ve got your very own proxy server (socks5 server is the most versatile among all types of proxy servers including HTTP proxy and FTP proxy) that’s local, stable and in your perfect control for getting around all kinds of firewalls. Screw all those obsolete online proxy server lists with unusable proxy servers!
I haven’t used it yet but a program like FoxyProxy or Proxifier can help make it easier to enable this kind of system. Those two applications were recommended to me by security-conscious friends.
—————————————–
Once you’ve got that setup, you can put a shortcut on your desktop of wherever that lets you start it quickly. Make the Target of the shortcut look something like this and it’ll start your new Saved Session but quick.
C:\Users\Lee\Programs\putty.exe -load “enable proxy tunnel”
And if the Saved Session has a hostname that looks something like this, you won’t have to type in the username, only the password
User@lee.org
—————————————
Ok, now you’re ready to run VNC through an SSH proxy tunnel. I found instructions on DSLReportts.com that work. This worked for me in about 10 minutes :-)
Run putty and setup an SSH connection and tunnel to the VNC server.
In this example we have setup an ssh connection to YOUR_IP_ADDRESS_HERE and given
it the session name BBR .
Finally set up a tunnel from port 5900 to your computer to port 5900 on
the VNC server. (as shown below)
Now you must save the session otherwise you’ll need to do it all again
next time you make a connection.
Open the session and make a connection to the SSH server.
Step 4.:
Run the Ultra VNC viewer and make a connection to localhost:5900.
You should have a login prompt from the VNC server machine now.
Could someone please offer one reason why the iTunes interface isn’t completely worthless?
It’s worse than worthless because I keep throwing time at it just to get a few freaking songs and movies put onto my iPhone and nothing is freaking happening.
iTunes wants to “own” my music and video collection but it does a crappy job of finding it (how the frig do you tell it “Look in folder x for my music?) and just as crappy job of sorting it (one giant list of 8,500 media files is NOT helpful). It wants to copy all my files to one central location for no effing purpose. It can’t even tell (or be told) that a file it previously found isn’t there any more.
I could rant for 10 paragraphs about the worthlessness of this interface. Here’s just an outline.
CRAZY slow – clicking most anything takes a full 0.5 seconds for a response and I never see an hourglass cursor. And that’s just an “Eff you user, you learn to wait!”
INSANE menu choices – For instance, I can’t even look my iPhone preferences unless my iPhone is plugged in.
NO WAY to tell it simple things like “here is where you should look for my music”
AMBIGUOUS controls. If you “Delete” something in iTunes, are you deleting the content?
DOESN’T PLAY WELL WITH OTHERS. If you want to find the folder where you’ve put a piece of music, sure, you can do a “Get Info” to see what folder it’s in but then you have to go to Windows Explorer and navigate there by hand.
There’s tons of other examples. But I’ve spent enough time on this stupid program.
I wrote this little guide for my aunt. Her email password got hacked a while back. If you don’t currently do something similar, you should!
First, here is how to make a bad password that will get hacked:
Now here is how to make a good password that is easy to remember and won’t get hacked:
Change all your passwords to follow a pattern. Make the pattern something you can easily figure out but a password thief could never do.
That’s it!
Your final password should be between 9 and 12 characters. (some websites stupidly limit the length of your password, and you don’t want to have to use a different strategy on those sites, lest it be harder to remember.
You now have a REALLY GOOD PASSWORD that is REALLY EASY TO REMEMBER and REALLY HARD TO GUESS. And it’s DIFFERENT ON EVERY SITE so when one website gets hacked, the bad people don’t know your password on other sites!
————————————————–
If you have gmail, I strongly recommend you turn on 2-step verification.
How to enable it.
A friendly video that walks you through it.
Yes, it takes a little effort, but so does locking your front door when you go out.
Short story: last year I sat down at a public computer at City College. As I typed in my password, I got this chill, wondering if there might be a virus on the computer, sending my password off to some nefarious Russian hacker den or somesuch. So the first thing I did was enable 2-step verification.
Flash forward 3 months to this ABC News article that starts out “A computer virus found at the City College of San Francisco may have been part of an elaborate international scheme stealing students’ personal information for more than a decade.”
Yes, the bad people got my password. But my password strategy and 2-step verification protected me. Nuff said.